Category : Endpoint Forensics Link to heading
Scenario:
As a member of the Security Blue team, your assignment is to analyze a memory dump using Redline and Volatility tools. Your goal is to trace the steps taken by the attacker on the compromised machine and determine how they managed to bypass the Network Intrusion Detection System “NIDS”. Your investigation will involve identifying the specific malware family employed in the attack, along with its characteristics. Additionally, your task is to identify and mitigate any traces or footprints left by the attacker.
Tools:
-
Q1
What is the name of the suspicious process?
Running ./vol.py -f ~/Desktop/MemoryDump.mem windows.pstree I was able to locate a suspicious process named oneetx.exe. I googled oneetx.exe and discovered that it is malicious and related to the Amadey dropped malware.
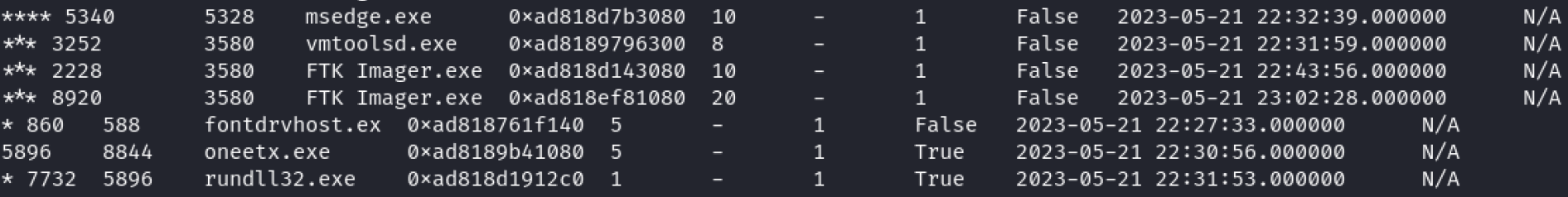
Answer = oneetx.exe
-
Q2
What is the child process name of the suspicious process?
From Q1 we can see that rundll32.exe is the child process.
Answer = rundll32.exe
-
Q3
What is the memory protection applied to the suspicious process memory region?
Running the plugin windows.malfind we see that the suspicious process region and protection is PAGE_EXECUTE_READWRITE.
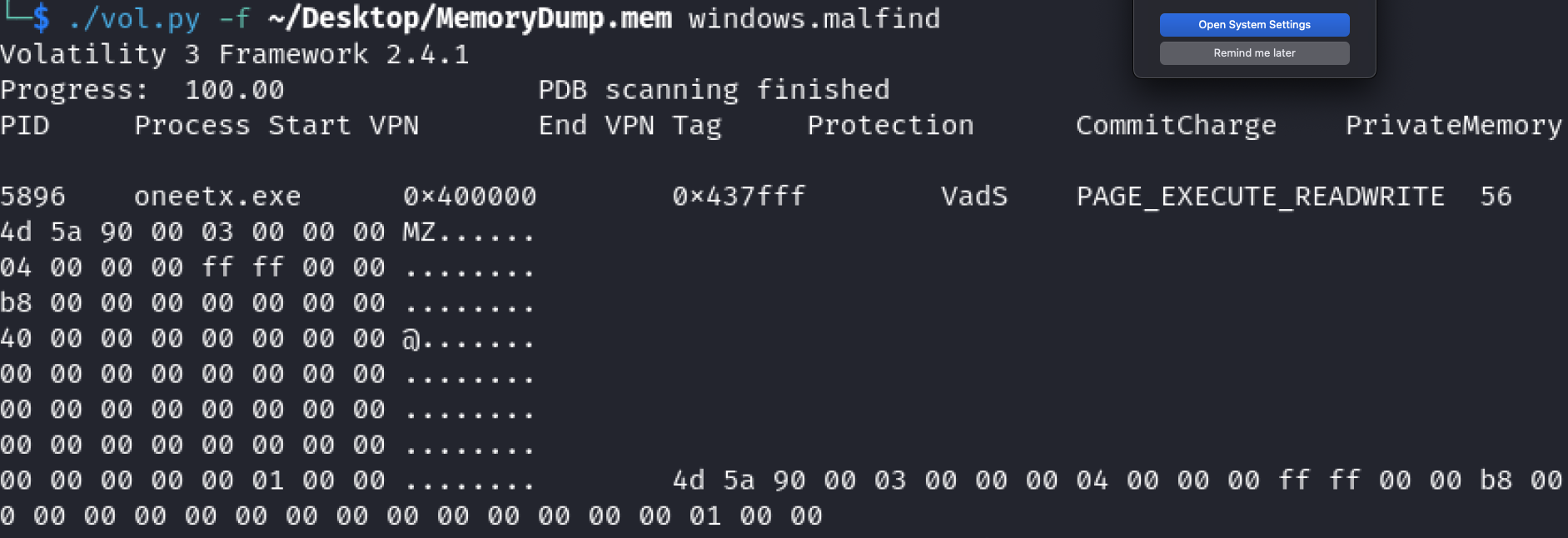
Answer = PAGE_EXECUTE_READWRITE
-
Q4
What is the name of the process responsible for the VPN connection?
I ran ./vol.py -f ~/Desktop/MemoryDump.mem windows.pstree to initial thoughts were that tun2socks.exe was the process responsible for the VPN connection due to its name. After googling the application I saw that Outline.exe is actually a VPN application.
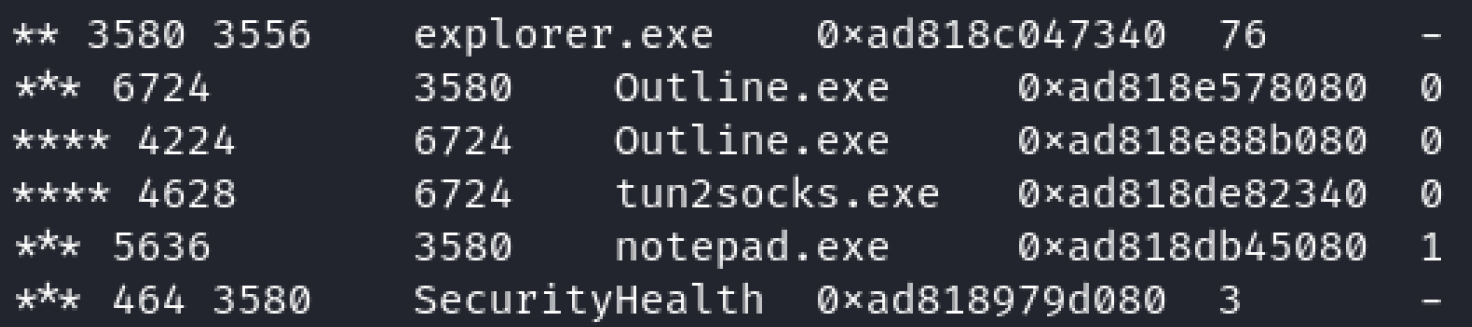
Answer = Outline.exe
-
Q5
What is the attacker’s IP address?
I ran ./vol.py -f ~/Desktop/MemoryDump.mem windows.netscan | grep "oneetx.exe" to find the connections related to the suspicious process and found the IP associated with it.
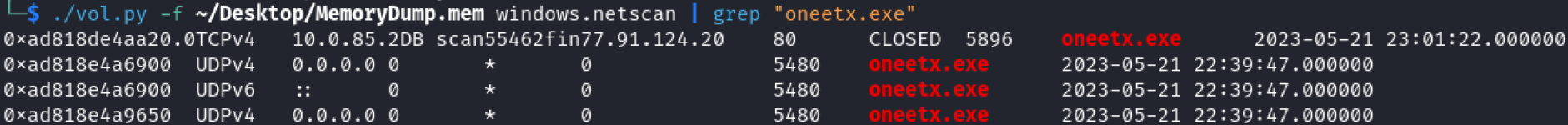
Answer = 77.91.124.20
-
Q6
Based on the previous artifacts. What is the name of the malware family?
I searched the IP on Cisco Talos and Virustotal. The later led me to abuse.ch which had a signature for RedLineStealer.
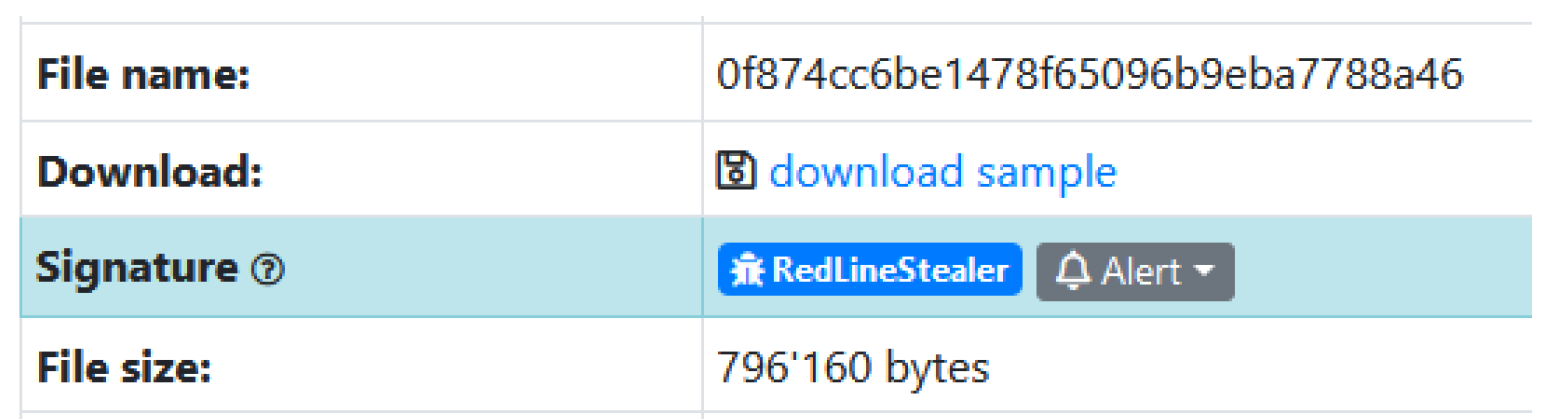
Running strings on MemoryDump.mem and grepping “redline” pulls a lot of hits as well to confirm.
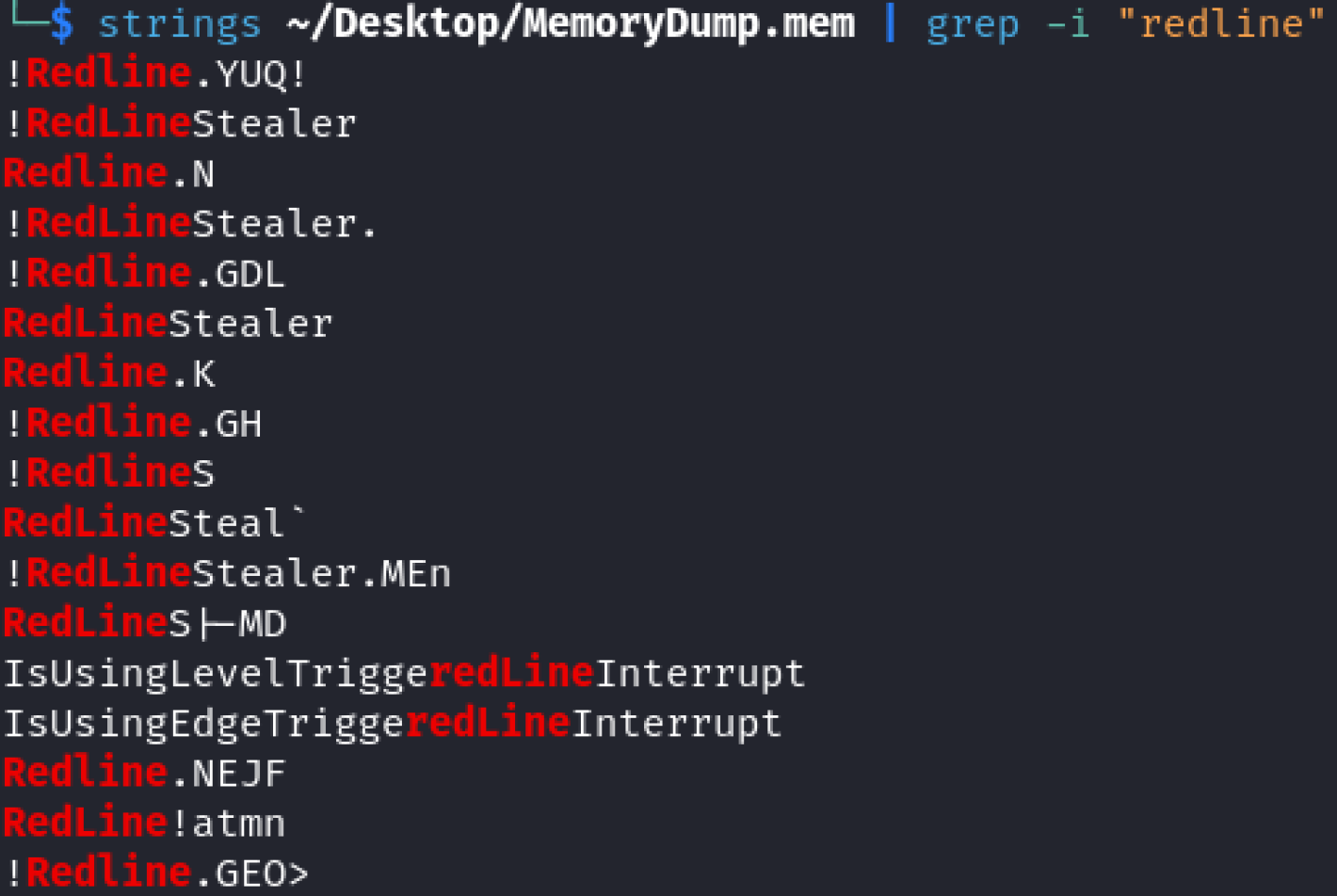
Answer = RedLine Stealer
-
Q7
What is the full URL of the PHP file that the attacker visited?
I searched strings on the MemoryDump.mem file and grepped the suspicious IP address.
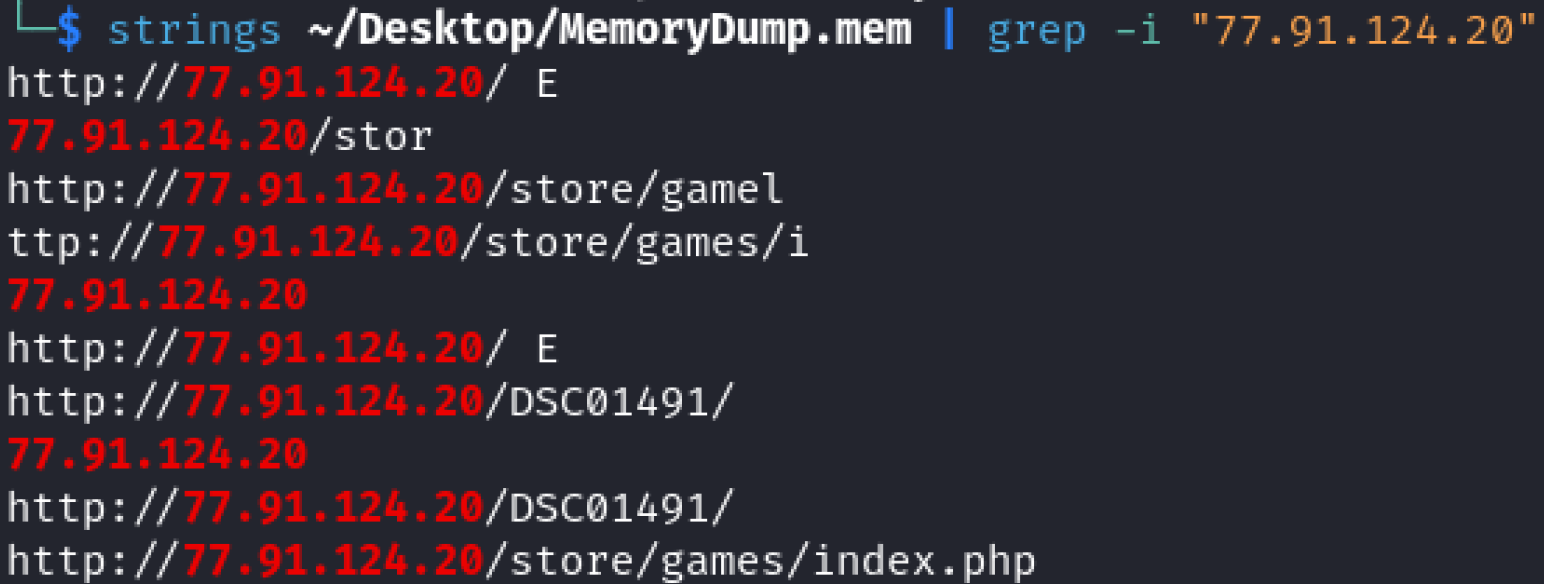
Answer = http://77.91.124.20/store/games/index.php
-
Q8
What is the full path of the malicious executable?
To find the full path of the .exe I used the plugin “filescan”, which scans for files in memory and used the malicious process name for the search.
/vol.py -f ~/Desktop/MemoryDump.mem windows.filescan | grep "oneetx.exe"
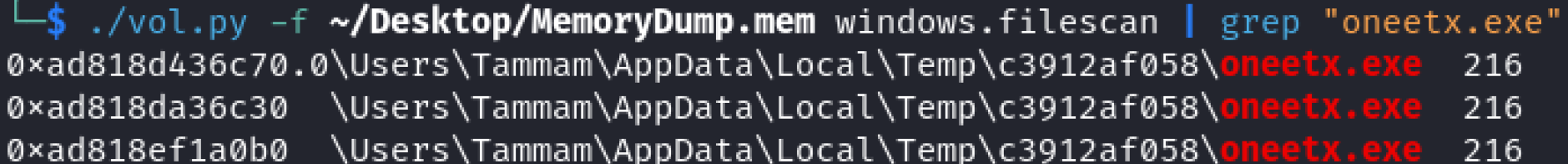
Answer = C:\Users\Tammam\AppData\Local\Temp\c3912af058\oneetx.exe